This documents my discovery of a leaky redaction technique used in the payment platform ‘Payeer’. I think it is a good demonstration of how redaction can be used but still not meet its intent.
Someone once asked me what I knew about the payment provider ‘Payeer’ as an alternative to Paypal, this prompted me to do a small bit of research and check them out. One thing that caught my eye was a feature on the marketing front page of payeer.com that appeared to be leaking real-time customer transaction details due to a bad implementation of redaction.
On the front page of payeer.com was a neat ‘Payeer statistics’ grid that displayed real-time customer transactions, since these were real transactions happening right now you could see a redacted version of the customers email address along with the address of who they were paying and the amount of the transaction (checkout the image below), new transactions were flying by each second and you really got a feel for the amount of transactions that Payeer has to handle.
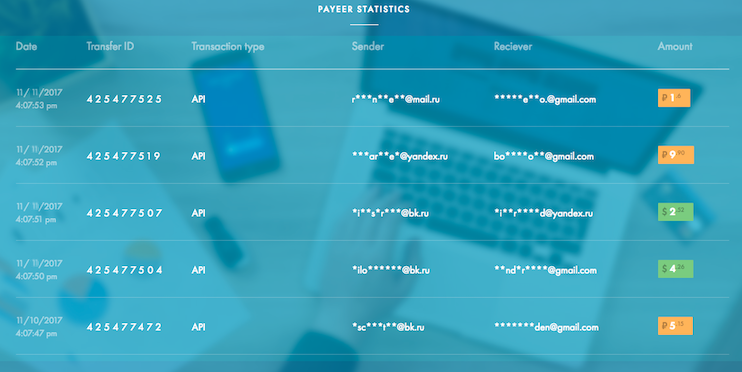
Curious if these were in fact real customer transactions I inspected the source to find that these transactions were being pushed to the marketing page through a web-socket directly from a Payeer API, what follows is an example of messages coming through from the WebSocket.
| uid | timestamp | amount | currency | from | to | category |
|---|---|---|---|---|---|---|
| 625906754 | 1910321873000 | 0.00136613 | BTC | e*****ge*@mail.ru | j**1****r@gmail.com | $1600 |
| 625906981 | 1910321905000 | 114.90 | USD | e**h*n***@gmail.com | s**o***l**@**otmail.com | $1600 |
| 625907531 | 1910321969000 | 1.74 | EUR | **c***ge*@mail.ru | **m*****k2@gmail.com | $1600 |
| 625908981 | 1910321979000 | 1.00246626 | BTC | e*****ge*@mail.ru | S**r****r@gmail.com | $1600 |
Though you can only see four messages in the data above I was sitting infront of hundreds of these messages and an issue became clear; the redacted email addresses were redacted in a nondeterministic fashion so when a payment took place with the same address a different part of that address was hidden each time, eventually leaking the entire address.
- l***h***s**@fakemail.com
- lu***i***8*@fakemail.com
- l*ke**ne**8@fakemail.com
Equals
I tested this on a few addresses and sure enough, I was able to reveal them. Generally it only took six messages to be able to unmask an entire transaction.
After spending some time trying to find a technical contact for Payeer I was able to report the issue, although they noted that they did not consider this a critical issue they did fix it within 48 hours from my initial report and pay a bounty for finding the issue.